Taming Network Storms: Understanding Spanning Tree Access Ports

Imagine a scenario where data packets on your network endlessly bounce between switches, consuming bandwidth and bringing your network to a screeching halt. This chaotic scenario, known as a broadcast storm, is precisely what spanning tree access ports are designed to prevent. These ports are essential components in any robust network, acting as gatekeepers against network loops and ensuring smooth data flow.
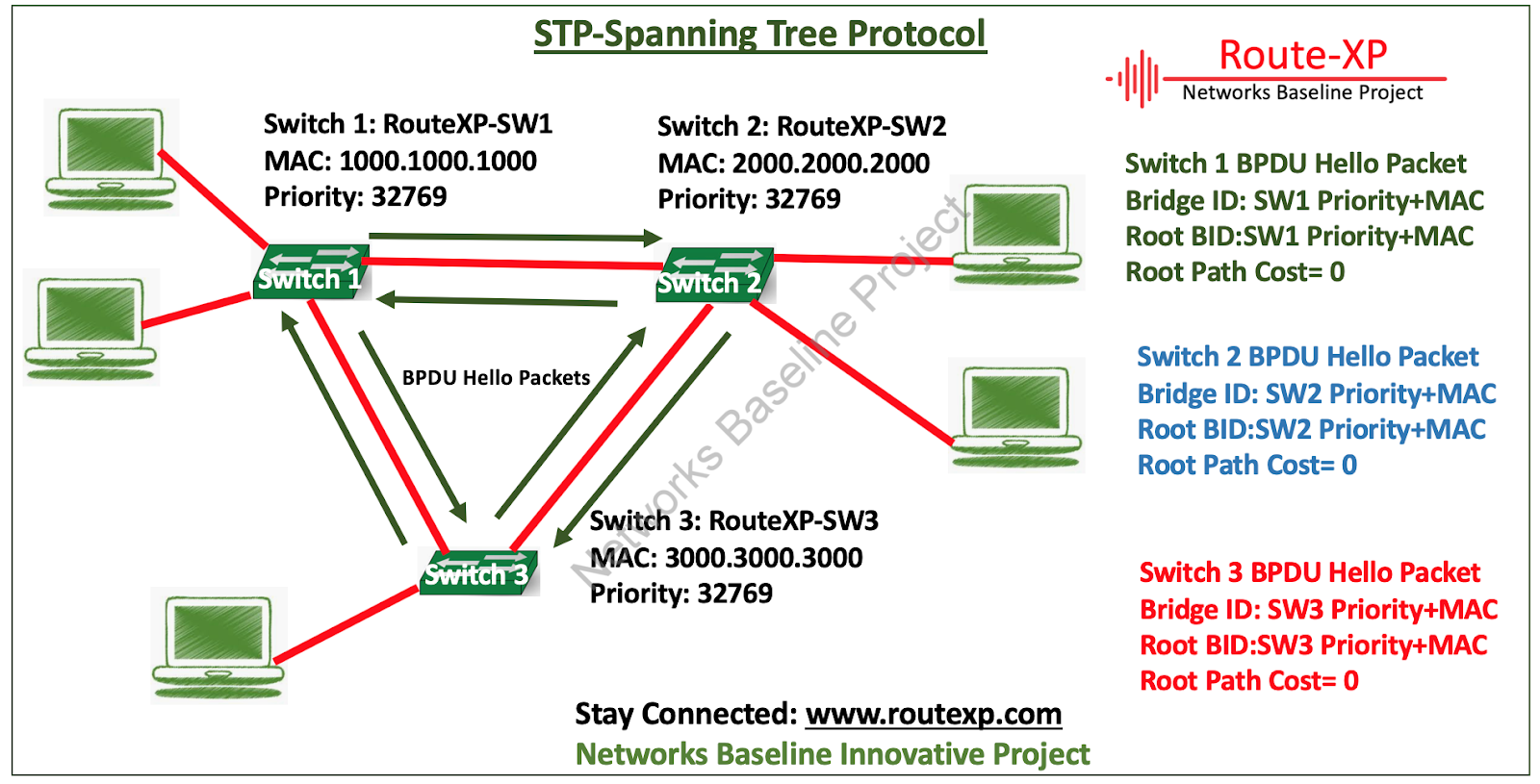
Spanning Tree Protocol (STP) and its more modern iterations, like Rapid Spanning Tree Protocol (RSTP) and Per-VLAN Spanning Tree Plus (PVST+), rely on the concept of designated ports and access ports to manage network traffic. A spanning tree access port is a specific port configuration on a network switch that connects to end-user devices like computers, printers, or IP phones. These ports are designed to carry user traffic only and do not participate in the spanning tree algorithm's loop prevention calculations.
The history of spanning tree access ports is intertwined with the development of the Spanning Tree Protocol itself, which was created by Radia Perlman in 1985. As networks grew in complexity, the risk of creating accidental loops became increasingly prevalent. STP, with its designated and access ports, emerged as a vital solution to this problem, ensuring network stability and preventing broadcast storms that could cripple communication.
The primary function of a spanning tree access port is to simplify the spanning tree topology. By designating a port as an access port, the switch effectively removes it from the spanning tree calculations. This reduces the computational burden on the switch and simplifies the overall spanning tree topology, making the network more efficient and easier to manage. Without access ports, managing a large network with multiple switches would be significantly more complex, with a higher risk of instability.
Understanding the configuration of spanning tree access ports is crucial for network administrators. By correctly configuring these ports, administrators ensure that end-user devices can communicate reliably without contributing to potential network loops. Misconfigurations can lead to instability, reduced bandwidth, and even complete network outages. The importance of access ports stems from their role in maintaining a loop-free topology while minimizing the processing overhead on the switching infrastructure.
A spanning tree access port is simply a switch port configured to only forward user traffic. It does not participate in the spanning tree algorithm and does not forward bridge protocol data units (BPDUs), which are used by the spanning tree protocol to detect and prevent loops. A simple example is a port on a switch connected to a workstation. This port should be configured as an access port as the workstation will not be involved in the spanning tree topology.
Benefit 1: Loop Prevention. Access ports contribute to preventing network loops by not participating in the spanning tree algorithm. This simplification reduces the chances of misconfigurations and ensures a stable network environment. Example: Imagine a user accidentally connects two ports on the same switch with a cable. If these ports are access ports, no loop will occur as they are excluded from the spanning tree calculation.
Benefit 2: Simplified Network Management. Access ports significantly simplify network management by reducing the complexity of the spanning tree topology. Example: A large network with hundreds of access ports connected to end devices is much easier to manage than a network where every port is part of the spanning tree calculation.
Benefit 3: Increased Network Efficiency. By reducing the processing overhead on switches, access ports contribute to increased network efficiency. Switches do not need to spend resources calculating spanning tree information for these ports, freeing up resources for data forwarding. Example: In a busy network, the reduced processing required by access ports translates into improved overall network performance.
Action Plan for Implementing Spanning Tree Access Ports: 1. Identify all ports connected to end-user devices. 2. Configure these ports as access ports using the appropriate command on your switch. For Cisco switches, the command is typically `switchport mode access`. 3. Verify the configuration by checking the port status. Successful Example: A network administrator configures all ports connected to workstations as access ports, ensuring a loop-free and efficient network.
Advantages and Disadvantages of Spanning Tree Access Ports
| Advantages | Disadvantages |
|---|---|
| Prevents loops | Limited functionality (no BPDU forwarding) |
| Simplified management | Not suitable for inter-switch links |
| Improved efficiency | Requires proper configuration to avoid issues |
Best Practices: 1. Always configure ports connected to end-user devices as access ports. 2. Verify the configuration after implementation. 3. Document your spanning tree configuration for future reference. 4. Regularly review and update your spanning tree configuration as your network evolves. 5. Use network monitoring tools to monitor spanning tree status and identify any potential issues.
Real Examples: 1. Connecting a workstation to a switch port. 2. Connecting a printer to a network. 3. Connecting an IP phone to the network. 4. Connecting a security camera to a network switch. 5. Connecting a point-of-sale system to a network.
FAQs: 1. What is a spanning tree access port? - A port configured not to participate in spanning tree calculations. 2. Why are access ports important? - They prevent loops and simplify network management. 3. How do I configure an access port? - Use the `switchport mode access` command (Cisco). 4. What is a BPDU? - Bridge Protocol Data Unit, used by STP. 5. What is STP? - Spanning Tree Protocol, used to prevent loops. 6. What is RSTP? - Rapid Spanning Tree Protocol, a faster version of STP. 7. What is PVST+? - Per-VLAN Spanning Tree Plus, a Cisco enhancement to STP. 8. What happens if I don't configure access ports correctly? - You risk network loops and instability.
Tips and Tricks: Use network management tools to visualize your spanning tree topology. Document your spanning tree configuration thoroughly. Stay updated on the latest spanning tree best practices.
In conclusion, spanning tree access ports are fundamental components of any stable and efficient network. They play a crucial role in preventing network loops, simplifying management, and optimizing network performance. By understanding the function and importance of these ports, network administrators can ensure a robust and reliable network infrastructure. Implementing best practices, like configuring all end-user device connections as access ports and regularly reviewing the spanning tree configuration, are vital steps towards a smoothly operating network. Taking the time to properly configure and manage your spanning tree access ports is an investment in the long-term health and stability of your network. Don't underestimate the power of these seemingly small configurations – they are the silent guardians protecting your network from the devastating effects of broadcast storms and ensuring reliable communication for all users. Regularly review and update your network documentation, including your spanning tree configuration, and consider implementing network monitoring tools for real-time insights into the health of your network's spanning tree implementation. By prioritizing these measures, you can avoid costly downtime and maintain a robust and efficient network infrastructure.
Postpartum fitness journey with a waist trainer regimen
Unlocking the magic of bluey and bingo imagery
Navigating identity in what it takes to be you manhwa